Introduction
We look at the great resource that is Windows Internals and take a closer look at Mandatory Integrity Control (MIC). The MIC mechanism is based on integrity levels to protect processes and objects from unauthorised access. The following table from Windows Internals 7th Edition Part 1 lists the different Windows Integrity Levels for Windows 10.
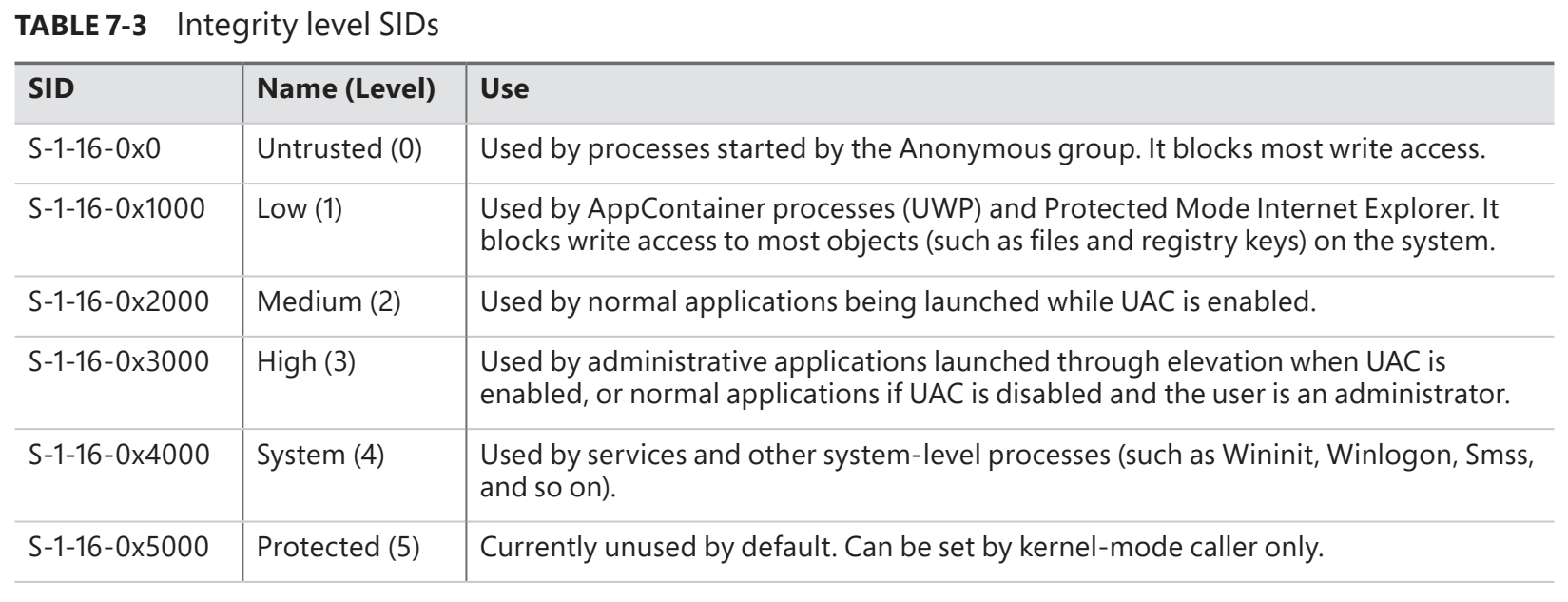
So when a non-privileged user (medium integrity) logs on to Windows, a kernel object called an Access Token is created. This token contains the user's identity and current privileges. From an attacker's perspective, this means that even if they manage to compromise a non-privileged user account (medium integrity), they will not be able to access processes or objects that have, for example, a high integrity level or a system integrity level.
Local Privilege Escalation: Insecure GUI
Even if you, as a medium-integrity user, cannot directly access the address space of a high-integrity process, e.g. through process injection, there are still scenarios where you can abuse the high-integrity process to escalate your local privileges. In my case, for example, by discovering the CVE-2022-0354 or LEN-76673 vulnerability related to the Lenovo Commercial Vantage tool and the way the Intel Management Engine runs software update packages (and other packages).
As usual, I logged into my Lenovo (as usual as an unprivileged user (medium integrity)) and launched the Lenovo Commercial Vantage tool in the same context (medium integrity). I got the suggestion for the Intel ME software update Intel Management Engine Firmware 11.8.90.3987 and started the installation. The Intel ME update then initialised immediately, but compared to other updates I have done with the Lenovo Commercial Vantage Tool, I found it strange that a Windows Command Shell window opened during the update. Although it was not possible to run a command directly from the command line, I was curious and used Process Explorer to see at what integrity level the open update window was running.
As suspected, the corresponding process, cmd.exe, was running at system integrity level. Despite the fact that no direct commands can be executed at the command prompt, there is still a way (insecure GUI) to use the privileged cmd.exe (system integrity) process to escalate from an unprivileged user (medium integrity) to system privileges. We simply use the context menu of the command line window of the privileged process cmd.exe to switch from medium integrity to system integrity. In the case of CVE-2022-0354, see the video below.
According to Lenovo, the vulnerability is in the legacy packaging process for system updates. To address the issue, Lenovo PSRIT has corrected the packaging process for packages released after 25 February 2002. At the moment I am not sure if Lenovo has also fixed the affected legacy packages or only the packages that will be released after 25/02/2022. The last test where I was able to gain system privileges was on 2022-04-10 with the Intel Thunderbold Driver-10 [64] update package (video below). To be fair, the Intel Thunderbold Driver-10 [64] package was only identified a few days ago, in early April 2022. So far, the following packages are known and affected, allowing escalation from unprivileged users (Medium Integrity) to system privileges (System Integrity).
The German Federal Office for Information Security (BSI) has also issued a technical security advisory with the second highest risk level (level 4).
Finally, I would like to thank Lenovo and their employee Blake for their cooperation. More information about the vulnerability can be found on the Lenovo website.
Happy Hacking!
Daniel Feichter @VirtualAllocEx