Einleitung
Wir werfen einen Blick auf die großartige Ressource Windows Internals und betrachten das Thema Mandatory Integrity Control (MIC) etwas genauer. Der MIC-Mechanismus basiert auf Integrity Levels, um Prozesse und Objekte untereinander vor unberechtigtem Zugriff zu schützen. Die folgende Tabelle aus dem Buch Windows Internals 7th Edition Part 1 listet die verschiedenen Windows Integrity Levels für Windows 10 auf.
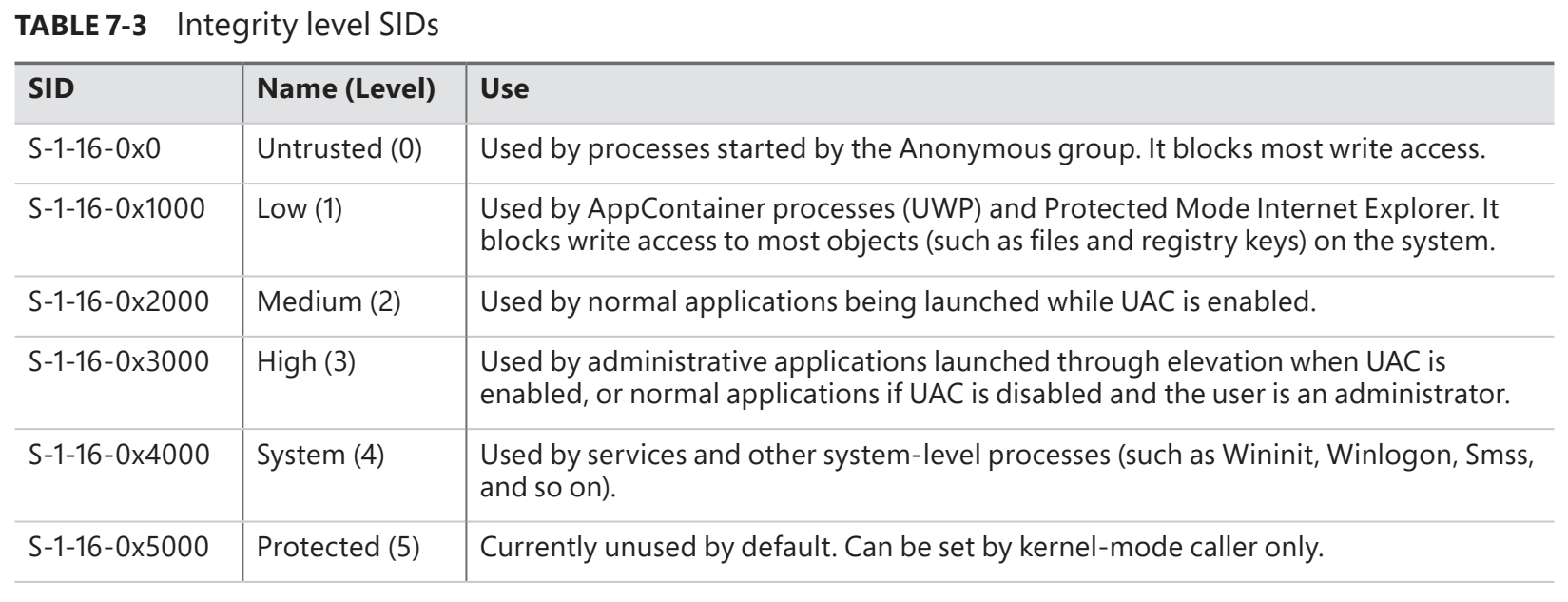
Wenn sich also ein nicht privilegierter Benutzer (mittlere Integrität) bei Windows anmeldet, wird ein Kernel-Objekt namens Access Token erstellt. Dieses Token enthält die Identität und die aktuellen Berechtigungen des Benutzers. Aus Sicht eines Angreifers bedeutet dies, dass selbst wenn es ihm gelingt, ein nicht privilegiertes Benutzerkonto (Medium Integrity) zu kompromittieren, es ihm nicht möglich ist, auf Prozesse oder Objekte zuzugreifen, die z.B. eine hohe Integritätsstufe oder eine Systemintegritätsstufe aufweisen.
Local Privilege Escalation: Insecure GUI
Auch wenn Sie als Benutzer mit mittlerer Integrität nicht direkt auf den Adressspeicher eines Prozesses mit hoher Integrität zugreifen können, z. B. durch Prozessinjektion, gibt es immer noch Szenarien, in denen Sie den Prozess mit hoher Integrität missbrauchen können, um Ihre lokalen Berechtigungen zu erweitern. In meinem Fall zum Beispiel durch die Entdeckung der Sicherheitslücke CVE-2022-0354 oder LEN-76673 im Zusammenhang mit dem Lenovo Commercial Vantage Tool und der Art und Weise, wie die Intel Management Engine Software Update Pakete (und andere Pakete) ausführt.
Wie üblich meldete ich mich an meinem Lenovo an (wie üblich als unprivilegierter Benutzer (mittlere Integrität)) und startete das Lenovo Commercial Vantage Tool im gleichen Kontext (mittlere Integrität). Ich erhielt den Vorschlag für das Intel ME Software Update Intel Management Engine Firmware 11.8.90.3987 und startete die Installation. Danach wurde das Intel ME Update sofort initialisiert, aber im Vergleich zu anderen Updates, die ich mit dem Lenovo Commercial Vantag Tool durchgeführt habe, kam es mir seltsam vor, dass sich während des Updates ein Windows Command Shell Fenster öffnete. Obwohl es nicht möglich war, einen Befehl direkt über die Kommandozeile auszuführen, war ich neugierig und untersuchte mit Hilfe des Prozessexplorers, mit welcher Integritätsstufe das geöffnete Updatefenster ausgeführt wurde.
Wie vermutet, wurde der entsprechende Prozess cmd.exe in der Systemintegritätsstufe ausgeführt. Trotz der Tatsache, dass keine direkten Befehle in der Eingabeaufforderung ausgeführt werden können, gibt es immer noch eine Möglichkeit (unsichere GUI), den privilegierten Prozess cmd.exe (Systemintegrität) zu verwenden, um von einem unprivilegierten Benutzer (mittlere Integrität) auf Systemprivilegien zu eskalieren. Wir verwenden einfach das Kontextmenü des Befehlszeilenfensters des privilegierten Prozesses cmd.exe, um von mittlerer Integrität auf Systemintegrität zu wechseln. Im Fall von CVE-2022-0354 sehen Sie sich das Video unten an.
Nach Rücksprache mit Lenovo liegt die Schwachstelle im Legacy-Paketierungsprozess für Systemupdates. Um das Problem zu beheben, hat das Lenovo PSRIT den Paketierungsprozess für Pakete, die nach dem 25.02.2022 veröffentlicht werden, korrigiert. Im Moment bin ich mir nicht sicher, ob Lenovo auch die betroffenen Legacy-Pakete repariert hat oder nur die Pakete, die nach dem 25.02.2022 veröffentlicht werden. Der letzte Test, bei dem ich Systemprivilegien erlangen konnte, wurde am 2022-04-10 mit dem Intel Thunderbold Driver-10 [64] Update-Paket durchgeführt (Video unten). Fairerweise muss gesagt werden, dass das Intel Thunderbold Driver-10 [64] Paket erst vor wenigen Tagen, Anfang April 2022, identifiziert wurde. Bisher sind folgende Pakete bekannt und betroffen, die eine Eskalation von unprivilegierten Benutzern (Medium Integrity) zu Systemprivilegien (System Integrity) ermöglichen.
Das Bundesamt für Sicherheit in der Informationstechnik, kurz BSI, hat ebenfalls einen technischen Sicherheitshinweis mit der zweithöchsten Gefährdungsstufe (Gefährdungsstufe 4) veröffentlicht.
Abschließend möchte ich mich bei Lenovo und dem verantwortlichen Mitarbeiter Blake für die gute Zusammenarbeit bedanken. Weitere Informationen zur Schwachstelle finden Sie auf der Website von Lenovo.
Happy Hacking!
Daniel Feichter @VirtualAllocEx